Retrieval Augmented Generation
Mastering RAG Systems: The Definitive Guide to Retrieval-Augmented Generation
Retrieval-Augmented Generation (RAG) is a sophisticated AI architecture that optimizes the performance of Large Language Models (LLMs) by grounding them in authoritative, external knowledge bases in real-time. Unlike static models limited by their training data, RAG systems dynamically “look up” relevant document chunks and proprietary data during the generation process, effectively eliminating hallucinations and ensuring that every AI response is factually accurate, contextually relevant, and fully traceable to its source.
RAG Systems FAQ Center
Explore our comprehensive knowledge base covering RAG technology, document analysis, AI accuracy, security, and best practices
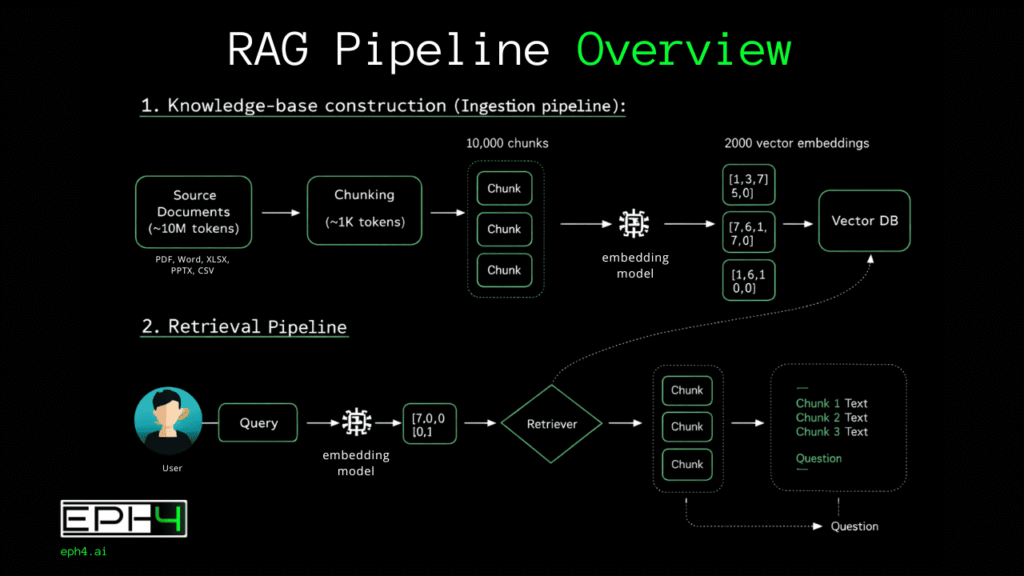
Understanding RAG Systems
Learn the fundamentals of Retrieval Augmented Generation, vector embeddings, semantic search, and how RAG transforms document analysis.
EPH4 Architecture & Speed
Learn about our sub-second injection pipeline, hybrid search technology, re-ranking algorithms, and enterprise-grade performance.
AI Hallucination Prevention
Discover how RAG reduces AI hallucinations through source grounding, citation tracking, and verified document retrieval techniques.
Document Processing & Formats
Everything about supported file formats including PDF, Word, Excel, PowerPoint, CSV, and how documents are extracted and chunked.
RAG vs Traditional AI & LLMs
Understand the key differences between RAG and standard AI models, knowledge cutoffs, and why RAG outperforms ChatGPT for document queries.
Ephemeral Sessions & Privacy
Understand our privacy-first architecture with automatic 2-hour data deletion, no accounts required, and complete session isolation.
Data Security & Encryption
Explore AES-256 encryption, data isolation, GDPR compliance, and enterprise security measures protecting your sensitive documents.
Use Cases & Applications
Discover how finance, legal, research, consulting, and other industries leverage RAG for document analysis and decision-making.
Accuracy & Source Attribution
Learn about confidence scores, source citations, verification methods, and how RAG maintains traceable, auditable responses.
Agentic RAG
Full overview on Agentic RAG, Pros and Cons. How Agentic RAG works, what are its benefits, use case scenarios and best practices.